A campaign was discovered, in which threat actors used Microsoft Build Engine (MSBuild) to filelessly deliver Remcos remote access tool (RAT) and password-stealing malware commonly known as RedLine Stealer.
The threat actors began infiltrating Remcos RAT, Quasar RAT, and RedLine Stealer payloads onto their victims’ computers last month. Once they are installed, they can be used to collect keystrokes, credentials, and screen snapshots, disable anti-malware software, and fully take over the devices remotely. To make matters worse, the malware will also scan for web browsers, messaging apps, and VPN, and cryptocurrency software to steal user credentials.
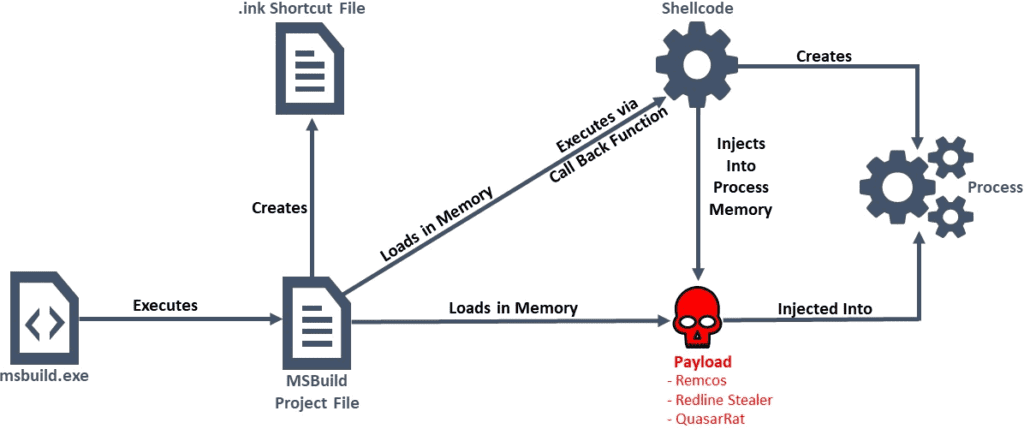
This campaign, which has low or zero detections on antivirus tools, appears to have begun in April 2021 and was still ongoing as of May 11, 2021.
The malicious MSBuild files observed in this campaign contained encoded executables and shellcode, with some, hosted on Russian image-hosting site, “joxi[.]net.”



