
Celestix Networks, Inc.
Americas: +1 510 668 0700
EMEA : +44 20 3900 3737
Asia : +65 6958 0822
Japan : +81 3 5210 2991
Zero Trust security for IoT
The proliferation of IoT devices has led to an expanded attack surface, making traditional security models inadequate. IoT devices often lack robust security features, and they can be vulnerable to various threats, including malware, data breaches, and unauthorized access.
Zero Trust Security is a cybersecurity framework that challenges the traditional “trust but verify” model. In a Zero Trust model, trust is never assumed, and verification is required from anyone or anything trying to access resources inside or outside a network. This approach is particularly relevant to IoT security, where the notion of trust should be eliminated to protect sensitive data and critical systems.
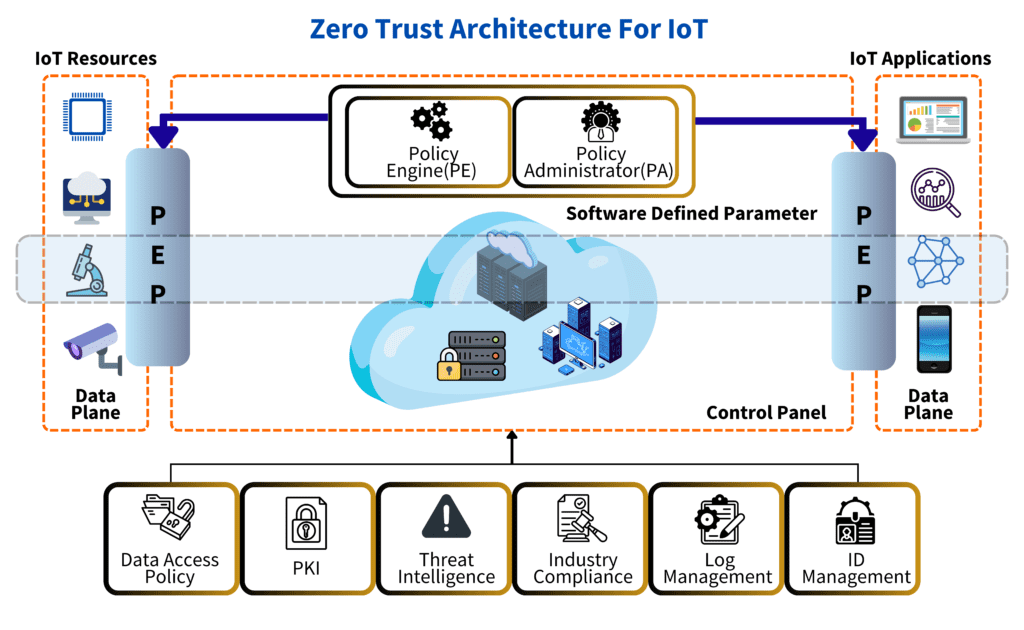
Figure 1: Zero Trust Architecture for IoT
The zero-trust model can face a few challenges:
Zero Trust Security is poised to play a crucial role in securing IoT ecosystems. Organizations must adapt to this evolving security paradigm to protect their IoT deployments effectively.
Stakeholders in IoT should prioritize Zero Trust Security by implementing its principles and strategies to enhance the security and resilience of IoT ecosystems.
In conclusion, Zero Trust Security is an essential framework for addressing the unique security challenges posed by IoT. As the IoT landscape continues to expand, organizations must embrace Zero Trust to ensure the confidentiality, integrity, and availability of their IoT resources. Through careful planning, implementation, and ongoing monitoring, Zero Trust can provide the necessary protection to safeguard IoT ecosystems in an ever-evolving threat landscape.

Celestix Networks, Inc.
Americas: +1 510 668 0700
EMEA : +44 20 3900 3737
Asia : +65 6958 0822
Japan : +81 3 5210 2991