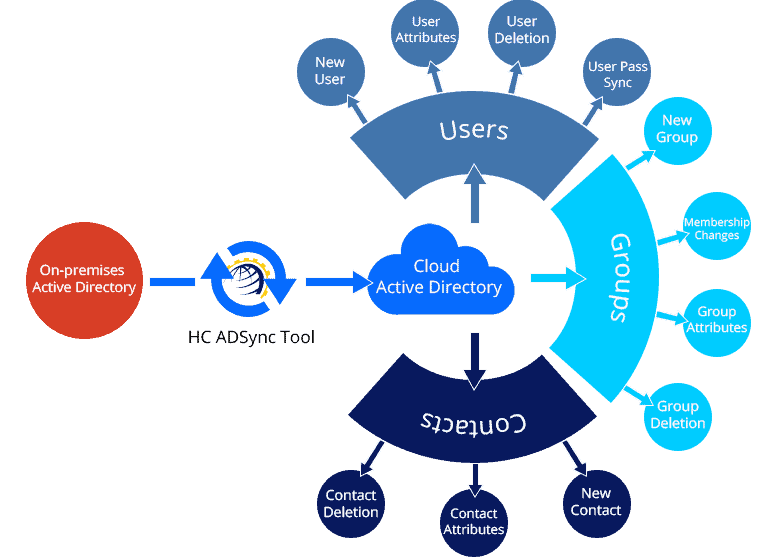
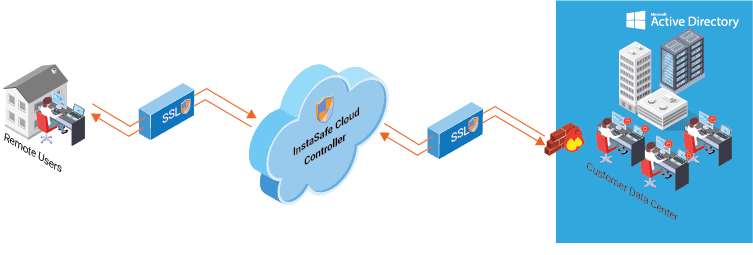
Traditional VPN Solutions are Highly Unsecured
In the modern age, businesses don’t work out of just one place. They are spread across multiple site locations to help serve the customers better. In such a scenario, the easiest way to interconnect two or more site locations is to use a traditional VPN. However, little do the businesses know how unsecured such a set up is. While it does the job of connecting the places, it leaves the complete network exposed to the internet for easy exploitation. For instance, it requires Inbound firewall rules for several ports, which makes the network vulnerable.