
Celestix Networks, Inc.
Americas: +1 510 668 0700
EMEA : +44 20 3900 3737
Asia : +65 6958 0822
Japan : +81 3 5210 2991
Secure cloud computing environment against external and insider threats with InstaSafe.
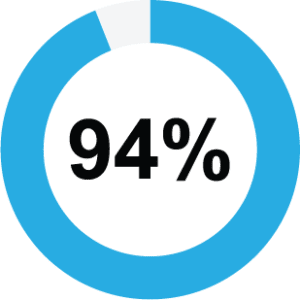
The advent of the cloud as an agile and scalable alternative to on premise data centers is inevitable. Organisations leverage 5 different cloud platforms on an average. Organisations may use multiple cloud platforms to save redundant costs and ensure flexibility.
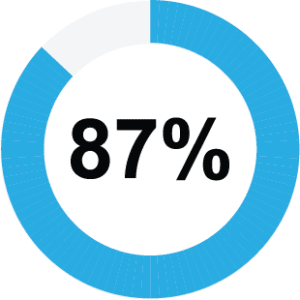
Cloud platforms are increasingly being preferred by businesses to improve scalability and operability while reducing costs.
Traditional security solutions don’t cope with the everchanging cloud access management.

Traditional Security Tools are not equipped for secure digital transformation.

Traditional solutions don’t account for BYOD policies and cloud access by unmanaged devices.

Traditional VPNs offer an inadequate level of security for modern cloud-native infrastructures, and don’t account for user context.

You cannot protect against attacks in the network which that you cannot see. Without a monitoring infrastructure to oversee your cloud environment, your cloud deployments are at greater risk.

Celestix Networks, Inc.
Americas: +1 510 668 0700
EMEA : +44 20 3900 3737
Asia : +65 6958 0822
Japan : +81 3 5210 2991