
Celestix Networks, Inc.
Americas: +1 510 668 0700
EMEA : +44 20 3900 3737
Asia : +65 6958 0822
Japan : +81 3 5210 2991
Endpoint security control is a core component of Zero Trust security model which secures application access and prevents data leakage with various control mechanisms. Endpoint is the entry point for enterprise network and resources. Having better security controls at endpoint can help IT administrator prevent a large number of threats.
Prevents the user from performing actions such as Copy & Paste, Screen Capture, Screen recording and clipboard access
Display the watermark logo and text as a graphical overlay over the content displayed on the screen.
Allows IT administrators to block specific domain URL or IP addresses from accessing by user or user groups
Allows IT administrators to block end users from accessing specific applications installed on their devices.
Restrict users using Chrome browser from performing file downloads, opening developer tools, and taking print copy of the browser content.
Disconnect ZTNA agent in case there is no activity performed for a certain period of time or there is limited data transfer activity performed for a certain period of time.
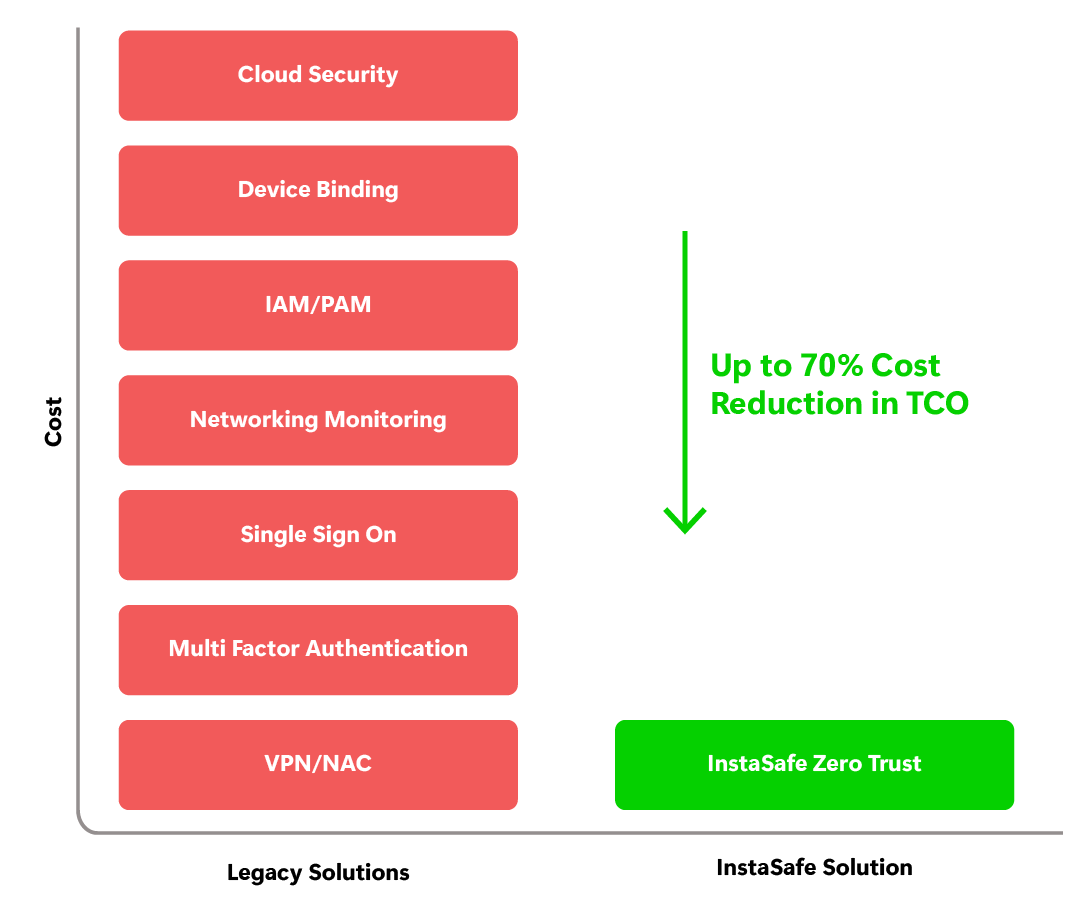
Prevents business critical data from being stolen or damaged by compromised endpoint devices.
Remote workers are ensured that the data is accessed through secured way and critical data is not stolen or stored on local machine.
Ensures that data is always being handled securely either by internal employees or third party workers, while protecting data breaches from threats arising from the endpoint.
Achieve better compliance with regard to how data is being accessed, stored, and protected.
InstaSafe integrates seamlessly with every internal applications, databases, and cloud





Celestix Instasafe MFA, powered by the Authenticator Application supports and complements InstaSafe’s other Zero trust capabilities

Celestix Networks, Inc.
Americas: +1 510 668 0700
EMEA : +44 20 3900 3737
Asia : +65 6958 0822
Japan : +81 3 5210 2991