
Celestix Networks, Inc.
Americas: +1 510 668 0700
EMEA : +44 20 3900 3737
Asia : +65 6958 0822
Japan : +81 3 5210 2991
Azure is a comprehensive set of cloud services that developers and IT professionals use to build, deploy, and manage applications through Azure global network of datacenters. Integrated tools, DevOps, and a marketplace support you in efficiently building anything from simple mobile apps to internet-scale solutions.
Azure offers in-built security functions such as Network Security Groups, Application Security Groups and others to secure your infrastructure on Azure, basis the shared responsibility model. However, while accessing various resources on the Azure Cloud, the network security levels are highly limited when using Azure’s own security functions, as it is restricted to IP address and port-based access controls. This limited control is contradictory to the granular identity-based access controls that enterprises typically implement within their infrastructure.

Azure Network Security Groups allow you to limit access to the VMs, Databases, and other such resources based on source IP address. Typically, the source IP address is your own set of public IP addresses. For individuals or companies that do not own any static public IP addresses, this security function provided by Azure is not applicable and hence, they are further exposed to a higher level of risk. Of course, additionally, the Network Security Groups can be defined to restrict access to specific ports.
This limitation of security functions on Azure are typically overcome by using site to site VPN connection to the on-premise data center and then backhauling all user traffic through remote access VPN setup for the users. However, such solutions are at best a patchy workaround and do not fully provide the level of security that is required by enterprises.
The major drawbacks of using legacy solutions are:
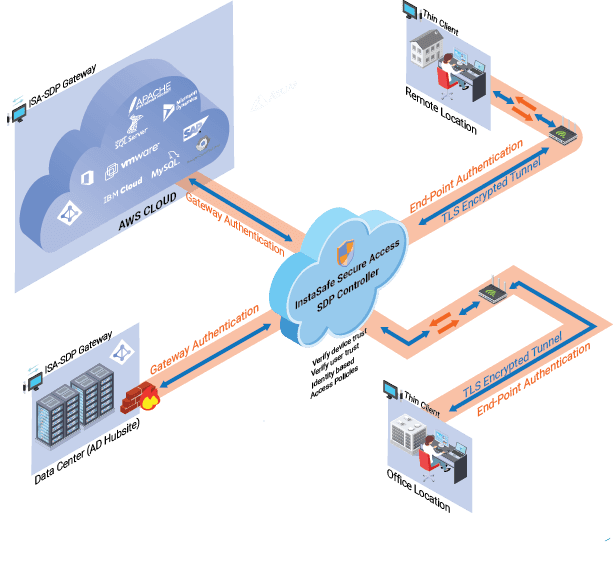
InstaSafe Cloud Access enables you to take complete control of who can access the applications, servers, databases, storage, and other resources on AWS
InstaSafe Cloud Access empowers you to create your own customized VPC peering between different regional VPCs
InstaSafe Cloud Access makes it easy for you to manage the access of employees and partners to specific applications with minimum fuss
DevOps require sysadmin (administrator) access to the resources on AWS. Administrator access is the favorite target of hackers due to the access level that sysadmins enjoy

Celestix Networks, Inc.
Americas: +1 510 668 0700
EMEA : +44 20 3900 3737
Asia : +65 6958 0822
Japan : +81 3 5210 2991