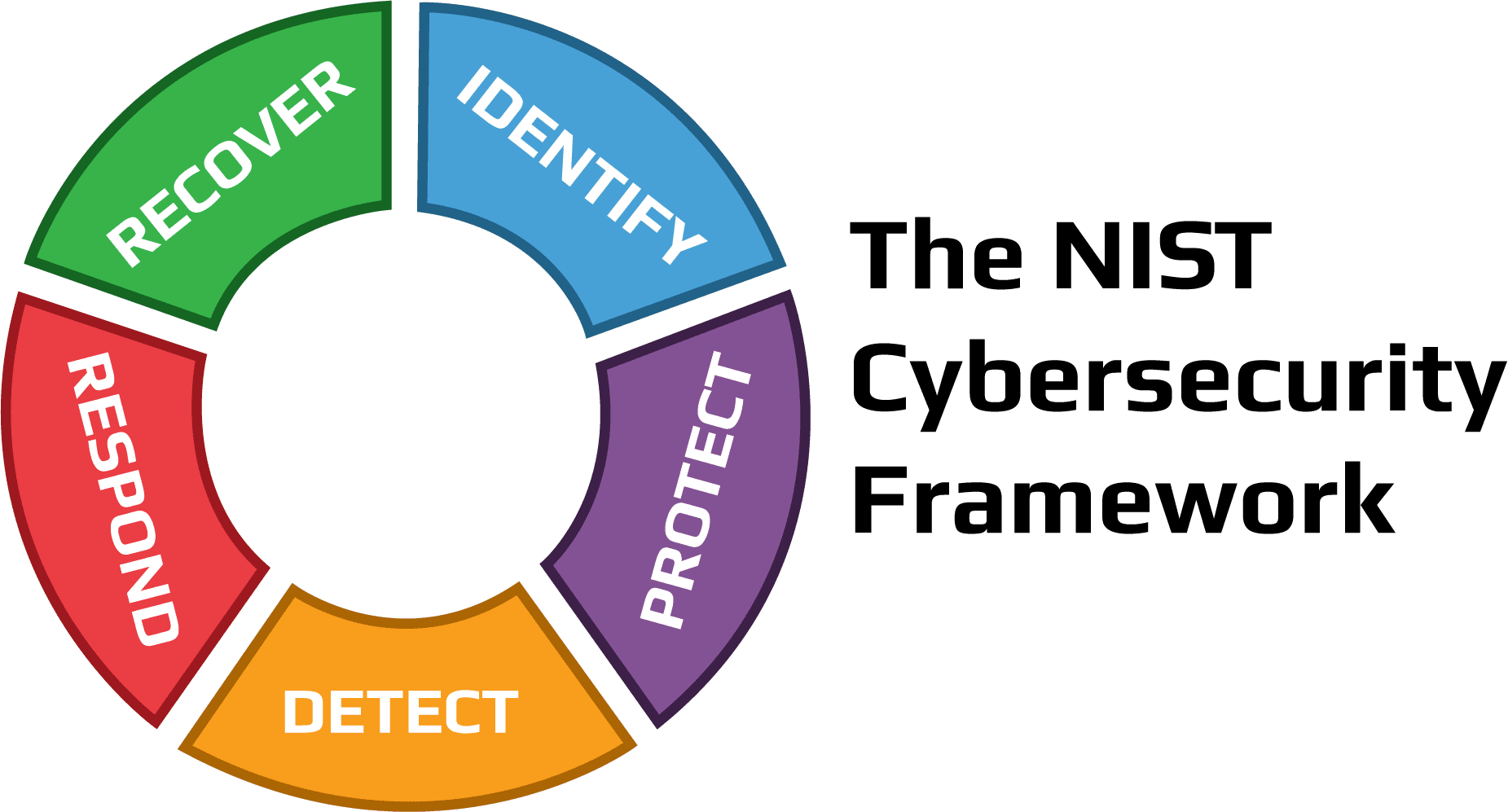
Why Internet of Things (IOTs) Infrastructure needs Zero Trust?
Introduction In today's interconnected world, the internet of things (IoT) has become an integral part of our daily lives. However, with the rapid expansion of IoT devices and networks, the…