
Celestix Networks, Inc.
Americas: +1 510 668 0700
EMEA : +44 20 3900 3737
Asia : +65 6958 0822
Japan : +81 3 5210 2991
With Zero Trust Enterprise Network, create secure, encrypted connections from user devices to the networks they wish to access.
Remove exposed IPs and make your network invisible to the internet.
All data in transit is end-to-end encrypted, and your traffic doesn't go through vendor machines.
Employ a default deny for all approach, and remove excessive trust from your network with a Zero Trust Network Security model.
Enable complete risk and trust assessment for every request for access continuously with zero trust network access solutions.
Enable secure access to thick client applications through IP Level Access.
Secure access to your SAP Applications by workforces situated anywhere.
Enable secure Desktop level PuTTY access to your Linux machines.
Remove exposed IPs and enable secure access to devices/application servers at the IP layer with Zero Trust Network implementation.



Only Authenticated Users and Authorized Devices are able to 'see' and access applications with zero trust security.
Gain a Bird’s eye view over all network traffic with zero trust model and identify threat vectors in real time.
Role based access to business applications on a need to know basis. One Click Access for better user experience.
Hardware Free. Rapidly deployable, scale as you go solutions
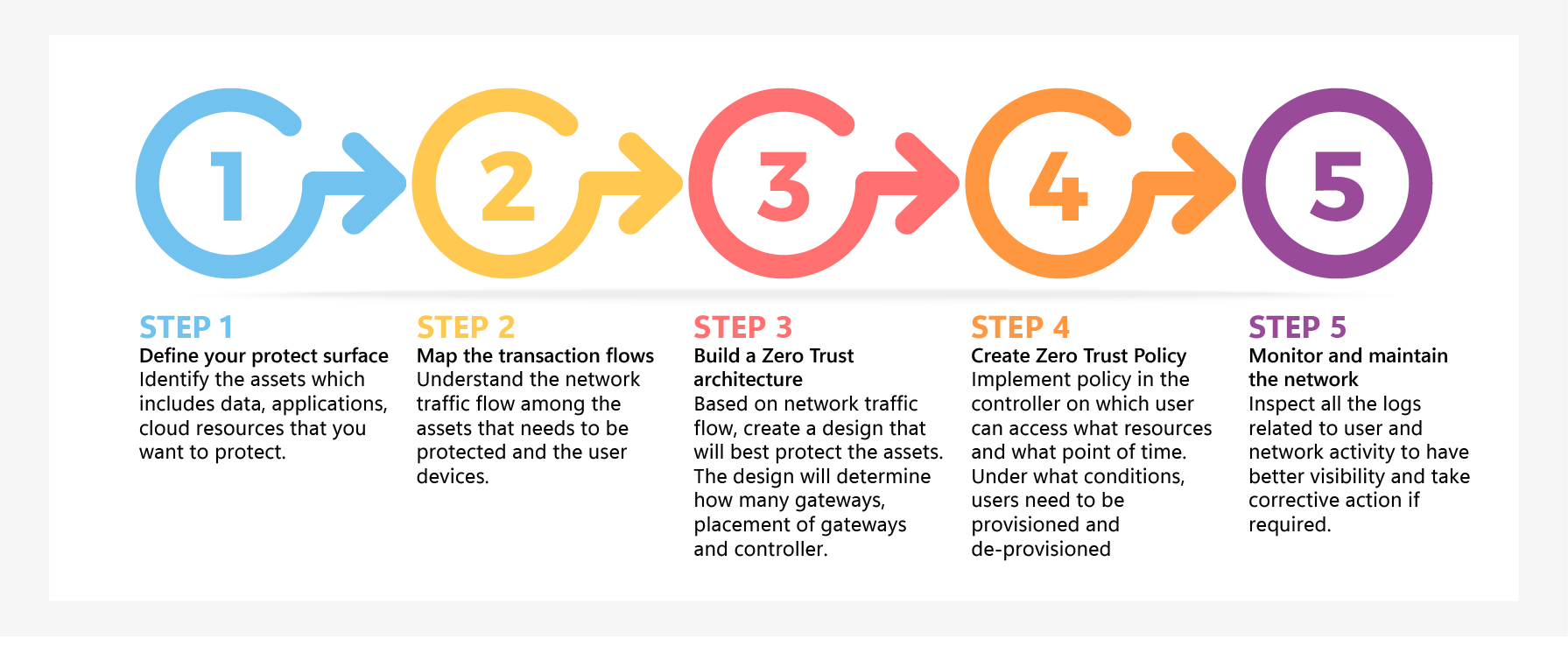
Zero Trust is a journey which every organization needs to take a phased approach of Zero Trust implementation and work on continuous refinement. There is a five step process for Zero Trust Implementation.
As a cloud agnostic, heterogeneous solution, InstaSafe has been built with the aim of providing seamless functionalities across hybrid and disparate environments, including wired, wireless, virtualized on-premises data centers, and cloud infrastructures. InstaSafe’s solutions have been designed to operationalize Zero trust policies across all environments and provide a seamless and unified user experience across any platform being used. InstaSafe helps in the implementation of security policies defined by teams to a very large range of network infrastructure and security products
InstaSafe’s Zero Trust Solutions are in line with the Zero Trust framework from the top down. InstaSafe enables IT teams to strategically implement Zero Trust across all portions of their enterprise networks. With powerful authentication and monitoring capabilities, InstaSafe starts with full visibility for all IP-connected devices across enterprise segments, including campus, data center, cloud and operational technology (OT) environments. The Zero Trust Network Access Solution provides deep inspection of device security and configuration state to determine the device risk posture. The InstaSafe policy engine translates the enterprise’s security policies and segmentation strategy into the rules applied by individual enforcement products based on the device’s risk posture and the user identity, and on this basis they classify an access request made by a device as trusted or untrusted. Additionally, InstaSafe’s zero trust approach to network security is easily integrable with monitoring and security tools like SIEMs and SAML/ADs, to simplify security management for teams.
Zero Trust systems are essentially touted to replace traditional security setups for more than 80% enterprises by 2023. This means that organization wide Zero trust Network strategy adoption needs to be one of the top priorities for CIOs and CISOs. Since Zero Trust is meant to be less of a single point solution, and more of a strategy, Zero Trust enabling technologies need to incorporate into every enterprise’s security stack to keep their security posture future ready
InstaSafe ZTAA is used to provide segmented application access by leveraging application specific tunneling. In essence, it provides application access without giving network access. InstaSafe Zero Trust Network Access (ZTNA), on the other hand, is used for very specific use cases that involve extending secure applications to thick client applications and extending secure access to devices/applications at the IP layer, as opposed to access at the application layer for ZTAA.
InstaSafe integrates seamlessly with every internal applications, databases, and cloud





Celestix Instasafe MFA, powered by the Authenticator Application supports and complements InstaSafe’s other Zero trust capabilities

Celestix Networks, Inc.
Americas: +1 510 668 0700
EMEA : +44 20 3900 3737
Asia : +65 6958 0822
Japan : +81 3 5210 2991