Introduction
V-OS Cloud provides many services that will help organizations to implement secure authentication mechanisms to protect their services easily and effortlessly.
V-OS Cloud OpenID Connect (OIDC) solution is based on the V-OS PKI Token solution hosted by the key components on V-OS Cloud, the V-OS Cloud Identity Management (IDM), and the V-Key app that is available on both Android and iOS. These cloud components are used for integrating the thrid-party services that you wish to implement secure authentication and authorization through directory services and authentication protocol connectors.
The services that have been verified to be compatible with the V-OS Cloud OIDC solution are:
- Salesforce
- Jamf
- Okta
- Delinea
- Oracle
- PingIdentity
- MiniOrange
- Citrix
- JFrog
Solution Architecture
V-OS Cloud OIDC solution consumes the cloud-hosted V-Key PKI suite, V-OS Cloud IDM, and V-Key app that are available to your users to connect from anywhere, anytime.
The following architecture diagram shows how V-OS Cloud interacts with OIDC enabled services.
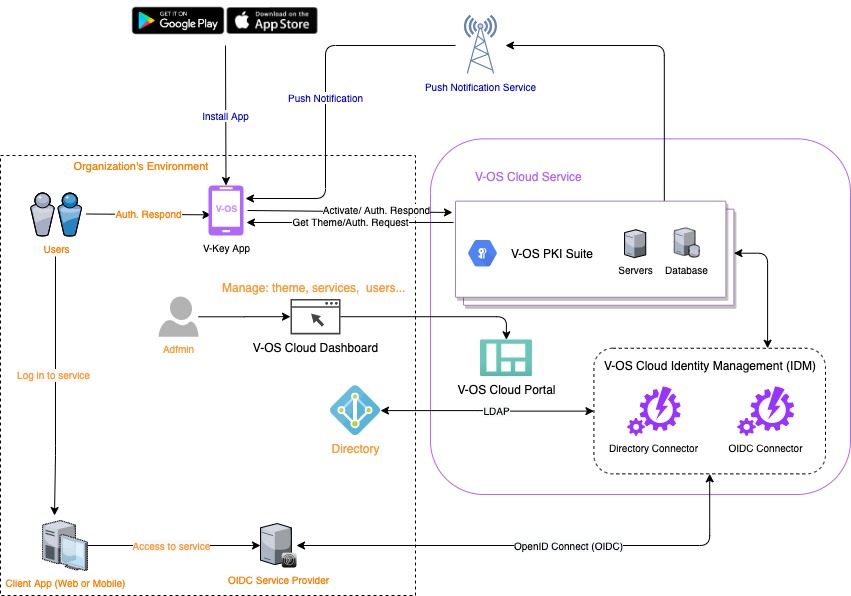
V-OS Cloud IDM acts as the OIDC Provider and uses an OIDC connector that enables OIDC proxy to send the authentication requests.
V-OS Cloud IDM provides directory connectors that allow you to authenticate users through existing directory credentials, both online directories, such as Azure Active Directory, JumpCloud, and on-premises directories, such as Active Directory in the local network for primary authentication before raising the secondary authentication to V-Key app.
V-OS Cloud Components
V-OS Cloud PortalThe V-OS Cloud Portal is the web interface where you can sign up, subscribe, manage subscriptions, services, payments, and orders. The URL to the Portal is https://cloud.v-key.com.V-OS Cloud DashboardThe V-OS Cloud Dashboard is the client area restricted by access accounts. You can log in to the Dashboard with either a root, admin, or supervisor account. You can configure (environments, services, and connectors), deploy services, and manage service users of your organization through the Dashboard. Only root and admin users have the right to do configurations and modifications in the Dashboard. Users with supervisor access right have only view access to the Dashboard. The URL to login to the Dashboard is https://cloud.v-key.com/login.V-OS Cloud IDMThe V-OS Cloud Identity Management (IDM) is the access gateway that handles communication between the V-OS Cloud and various components such as directories, RADIUS server, SAML server, etc. that are available in your organization for initiating and performing the authorization and authentication of end-users.V-Key AppThe V-Key app is a mobile app developed for V-OS Cloud that can be used to do 2nd factor authentication for service accesses. It serves as a virtual token to help end-users to manage accounts and do authentication approval. The V-Key app is mandatory for end-users to utilize the V-OS Cloud services if your organization subscribed to the Free or Professional plan. The V-Key app can be downloaded from the Apple App Store and Google Play Store. It is recommended to always upgrade your V-Key app to the latest version.
Organizational/Third-party Components
DirectoryThe directory service that the credentials of the end-users are stored. V-OS Cloud IDM will communicate to this directory by LDAP protocol to authorize users during user login, V-Key app activation, and first authentication. It is mandatory to expose this directory for V-OS Cloud IDM to query during authorization and authentication.
V-OS Cloud supports the following directories:
- Microsoft Active Directory: the directory that your organization installed on-premise and used to integrate with V-OS Cloud from outside of the enterprise network
- Azure Active Directory (AAD): the directory on Microsoft Azure Cloud Services
- Online 3rd Party Directory Services: other 3rd party directory services, such as JumpCloud, that provide online directory services
- OpenLDAP: an open-source software for directories that enterprises can use and deploy on their environment
- Other LDAPs: other LDAP-based authentication software/services that V-OS Cloud is compatible with
Note: If your organization doesn’t have any directory services or cannot enable the directory to integrate with V-OS Cloud, we have a solution to migrate your users’ credentials to our cloud, contact us at cloud@v-key.com for more details.
Third-party Service SubscriptionThe necessary subscription is required for the third-party service that needs to be seamlessly accessed through V-OS Cloud. The third-party service will be integrated with V-OS Cloud IDM by OIDC protocol. The third-party service acts as an OIDC service provider, and V-OS Cloud IDM acts as an OIDC Identity provider. V-OS Cloud IDM receives an OIDC authentication request from the third-party service, and triggers an authentication request with the V-Key app, then responds OIDC token to the third-party service.
Flow Diagram
The following diagram shows the communication flow in V-OS Cloud when a user tries to log in to the third-party service with V-OS Cloud OIDC solution integrated.
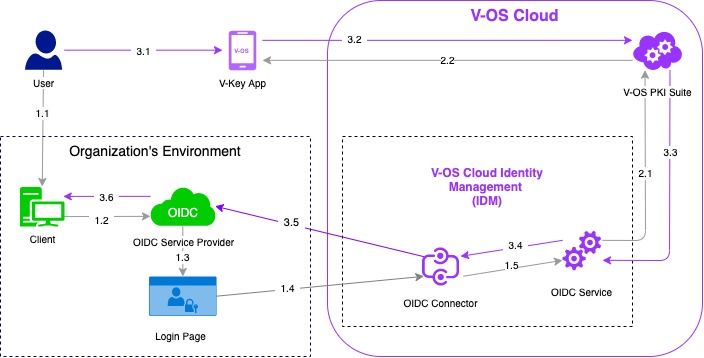
The sample flow of the V-OS Cloud OIDC solution is as follows:
Note: The primary directory is used for authenticating the user when logging in to the V-Key app. The secondary directory is used for authenticating the user when trying to connect to the VPN service. The primary and secondary directories can be the same directory or different directories. When a user tries to log in to the V-Key app, V-OS Cloud IDM queries the primary directory to authenticate the user. When a user tries to log in to the V-Key app, V-OS Cloud IDM queries the primary directory to authenticate the user.
- Steps 1.1 – 1.5: The user triggers the login request from the third-party service then redirected to the V-OS Cloud IDM login page.
- Steps 2.1 – 2.2: V-OS Cloud IDM triggers authentication request to the V-Key app on the user’s mobile device.
- Steps 3.1 – 3.6: The user confirms the login request on the V-Key app that will respond to V-OS Cloud IDM and then back to the third-party service to grant the login session.
