Introduction
V-Key MFA for Windows Logon improves security and streamline user authentication by leveraging multi-factor authentication (MFA) and advanced mobile-based authentication methods. It provides secure, seamless login experience across various Windows platforms and Windows Server environments using V-Key Smart Authenticator (VSA) App. It integrates push notifications and One-Time Password (OTP) authentication powered by the VSA authenticator.
Purpose
This document’s purpose is to describe the features of the V-Key MFA for Windows Logon and provide detailed instructions for installing it on your Windows machine.
Audience
This document is primarily intended for the Windows users who want to integrate V-Key MFA for Windows Logon into their machines.
Objectives
The main objective of the V-Key MFA for Windows is to integrate a PKI-based authentication system with secure push notifications and One-Time Password (OTP) verification, powered by the V-Key Smart Authenticator. This approach aims to enhance security within the Windows environment of the organization without sacrificing usability.
Specific Objectives:
- PKI Integration with Push Notifications: Implement PKI-based authentication that leverages secure push notifications through the V-Key Smart Authenticator to allow users to approve or deny logon requests on their mobile devices, ensuring certificate- backed authentication and added convenience.
- OTP Logon: Provide One-Time Password (OTP) functionality via the V-Key Smart Authenticator to offer an additional secure login method, complementing the PKI- based approach.
- Integration with Enterprise Infrastructure: Ensure seamless integration with Active Directory and other enterprise identity management systems to support domain- based authentication across the organization.
Features
This section outlines the features offered by V-Key MFA for Windows Logon.
User Type Detection
While using the Windows Logon, the system distinguishes between domain and non-domain users to tailor the authentication process.
- Domain Users: For domain-joined machines, authentication will integrate with Active Directory (AD) using PKI. OTP will be available as a fallback for users who face issues with certificate-based authentication.
- Non-Domain Users (Workgroup): For workgroup machines or local users, the logon process will rely on local account validation. PKI and OTP authentication will still be supported, even in the absence of Active Directory.
Remote Desktop Protocol (RDP) Support
The custom logon solution must support Remote Desktop Protocol (RDP), particularly for Windows Servers, where remote access is frequently required:
RDP for Windows Servers: The credential provider will support both PKI and OTP-based authentication during RDP sessions. Users connecting remotely will authenticate using the V-Key Smart Authenticator, ensuring secure access to Windows Server environments. Ulti-factor authentication (MFA) via PKI and OTP will be enforced for all RDP logon sessions, enhancing remote access security.
Authentication Methods
The logon solution will leverage two primary authentication methods:
- PKI (Primary): The main authentication method will be Public Key Infrastructure (PKI). Users will authenticate with digital certificates stored in the V-Key Smart Authenticator, ensuring a secure, certificate-backed logon.
- OTP (Fallback): In cases where PKI-based authentication is not available or fails, users will log in using a time-based One-Time Password (OTP) generated by the V-Key Smart Authenticator. This provides a secure, alternative authentication method.
Backup Options via V-Key Smart Authenticator
To ensure continuous access in case of issues with the primary authentication method, the V-Key Smart Authenticator app itself provides a backup:
V-Key Smart Authenticator Backup: Users will be able to generate backup One-Time Passwords (OTPs) directly via the V-Key Smart Authenticator app if the primary PKI authentication method fails or cannot be used. This ensures that even without additional hardware tokens or devices, users will have a secure backup method available.
Offline Access (No Internet Access)
During unavailability of internet access (e.g., network outages or remote environments), push notifications will not function, as they require server communication. In these cases, OTP authentication via the V-Key Smart Authenticator will ensure users can still log in securely.
Offline Logon via OTP: When the system detects no internet access, the credential provider will automatically switch to OTP-based authentication. Users will generate a time-based OTP from the V-Key Smart Authenticator and manually enter it into the logon screen. The OTP will be validated locally, allowing users to log in without needing an internet connection.
Scenarios for Offline Access: Offline logon is critical for environments with restricted network access, such as secure facilities or maintenance operations, or during network outages. By using OTP for offline access, users maintain secure access without requiring an active internet connection.
Supported Platforms
The V-Key Windows logon customization is designed to be compatible with the following operating system platforms
Operating Systems
- Windows 10 (Pro)
- Windows 11 (Pro)
- Windows Server 2016
Processor Architectures
- x64 (64-bit) architecture for all supported platforms
Virtual Environments
- VMware Workstation/ESXi
- Azure Virtual Machines (Windows)
Dependencies
- Microsoft .NET Framework 4.8 or higher
- V-Key Smart Authenticator client (latest version)
- Windows SDK
- Active Directory Integration (optional)
Configurations on IDM portal
V-OS Cloud Identity Management (IDM) portal needs to be configured to set up V-Key MFA for Windows Logon. Before that, following prerequisites need to be carried out.
Prerequisites
- Login IDM Portal with admin account.
- Setup a Directory & its Users. Refer Directory Configuration from Appendix section for the guidance.
- Configure Token Packs. Refer Taken Pack Configuration from Appendix section on how to configure token packs.
Steps to Configure
Follow below steps to set up Windows Logon on IDM Portal.
Step 1: Create an HTTPS Connector
- Navigate to Connector → HTTPS → Select to create HTTPS connector.
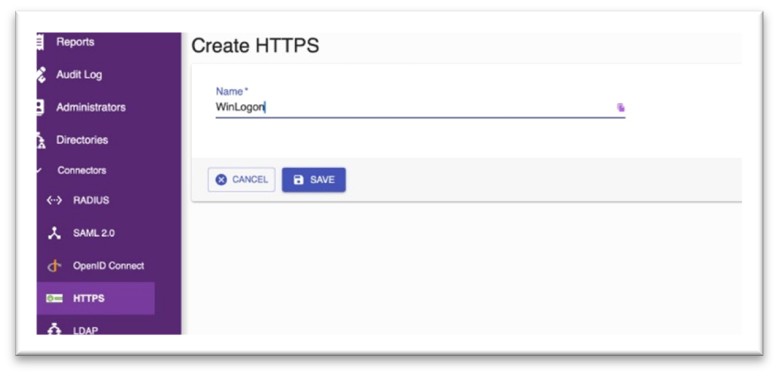
Fig 1: Create HTTPS Connector
- Assign suitable name for HTTPS Connector and Save it.
Step 2: Create HTTPS Service & Assign to the Token Pack
- Navigate to Services → Create → Select Windows Logon Authentication under HTTPS
Select the Subscription containing the Token Pack that you have configured as
- prerequisites.
- Select the Token Pack
- Input suitable name for the Windows Logon Service
- Select the Directory with the users that you have configured as a prerequisite
Select the HTTPS Connector created in Step 1
- Save the HTTPS Windows Logon Service
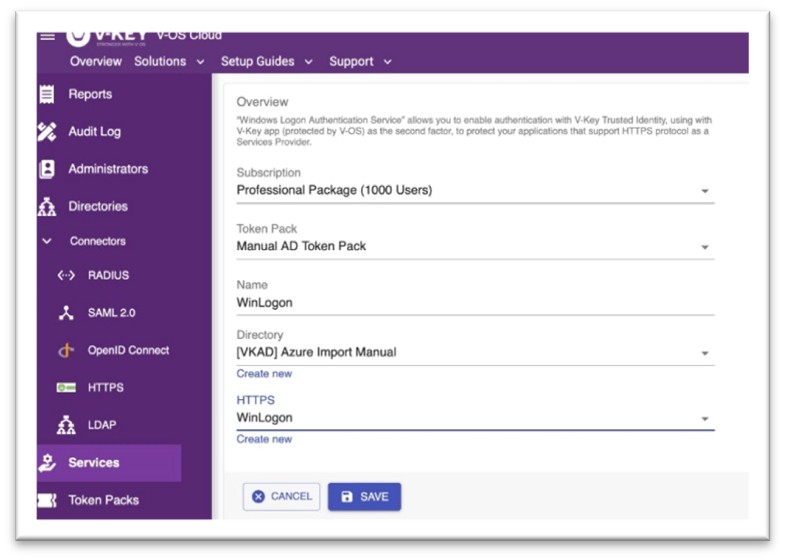
Fig 2: Create HTTPS Windows Logon Service
After creating WinLogon service successfully, select to generate OTP secret for the users
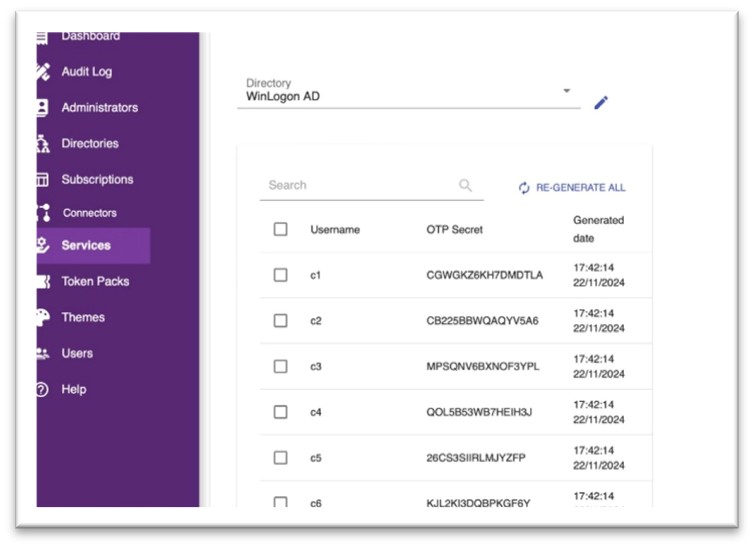
Fig 3: OTP Secret
Step 3: Service Verification
- Verify that the Windows Logon (WinLogon) service is created & assigned to the Token Pack successfully
- Navigate to Token Packs → Select to edit the Token Pack used by WinLogon service → Scroll to check the created WinLogon service in the list. Verify that the service is running.
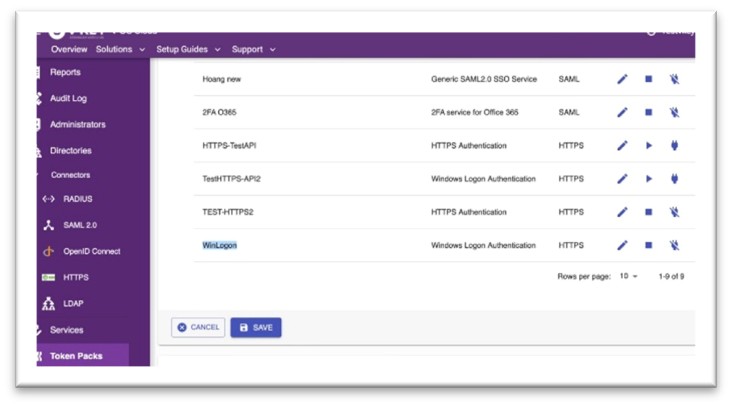
Fig 4: Service Verification
Step 4: Directory Verification
- Verify the directory which was setup for Token Pack
- From the edit Token Pack page, observe the Primary Directory → Check the corresponding directory which is used to enable Win Logon service.
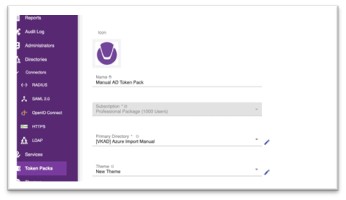
Fig 5: Directory Verification
Step 5: Activate user with VSA
- Install (V-Key Smart Authenticator) VSA app on mobile device
- On VSA app, activate the user from the Token Pack using Token Pack QR Code or Activation Code
- This successfully completes WinLogon service configuration on IDM Portal and VSA App.

Fig 6: VSA App Activation
Set up Windows Agent
Your Windows machine needs to be set up with V-Key MFA for Windows Logon.
- Open IDM Portal and created WinLogon connector. Copy the [Client ID] & [API Key] from this page.
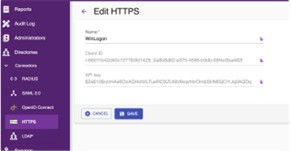
Fig 7: WinLogon Connector
- Run V-Key Windows Logon installer with the Administrator permission.
Fig 8: WinLogon Installer
- Agree to the [Term of Use & Privacy Policy] and click Install.
- Let the setup progress to check & download necessary components if needed (Visual Studio Build Tools & Windows Development Kits)
- Now set up V-Key Credential Provider.
- Paste the Client ID and API Key (copied from step 1) from IDM portal (HTTPS connector details session)
- Check or uncheck the [Remember Windows User Password] option. If checked, only the 1st time login with push authentication requires to input password. If unchecked, every time login with push authentication requires to input password.
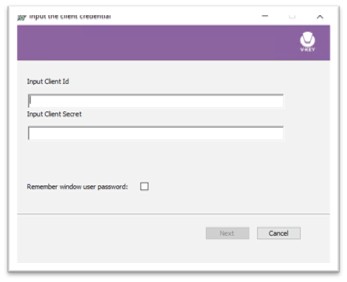
Fig 9: V-Key Credential Provider
- Once the installation is finished, log out of the account and check to see if the V-Key WinLogon service appears.
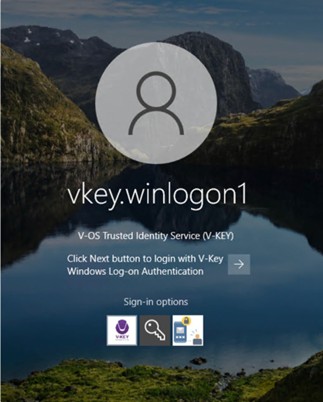
Fig 10: WinLogon Service
Authenticate Login Requests
- Once V-Key Logon Service appears on the login screen, select push authentication option, then click [Send push notification to V-Key app].
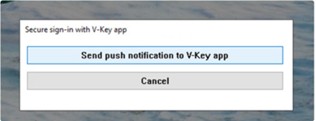
Fig 11: Push Notification
On VSA app with activated user, you will see the push authentication request.

Fig 12: Push Authentication on VSA App
After login request on VSA, if 1st time login gets successful, there will be a prompt message for offline OTP generated.
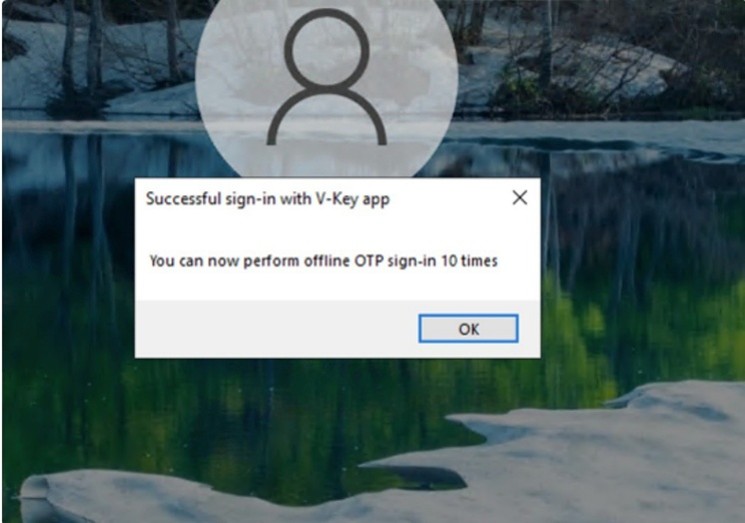
Fig 13: Offline OTP Generation
- After 1st successful login with push authentication, open the HTTPS service on IDM Portal & copy the OTP Secret (seed) of activated user.
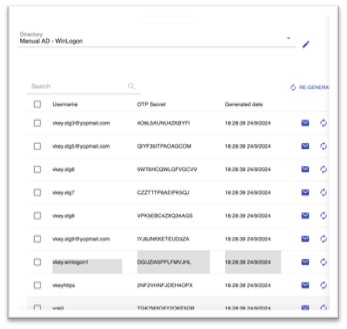
Fig 14: OTP Seed of Activated User
Paste the OTP Seed copied from IDM Portal to below URL.
otpauth://totp/WinOTP:winuser?secret=<OTP seed>&issuer=V-Key-WinLogon
Use above URL to generate QR code from any valid QR code generator. Then use VSA to scan generated QR Code.
Fig 15: VSA Screen
Note: From VSA latest versions (4.10.12 – iOS and 4.10.15 – Android) auto provisioning is supported and QR code need not be generated by users.
- From login screen on Windows, select OTP login from Sign-in options.

Fig 16: OTP Login
Get the OTP from VSA & input into OTP field on Windows login
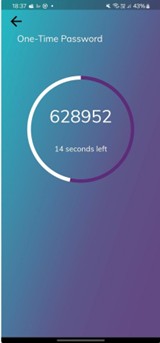
Fig 17: OTP for Windows Login
After inserting valid OTP in the time window, the login should be successful without any issue.
Uninstall Windows Agent
Open app manager from system & select to completely uninstall below 2 apps.
- V-Key Agent Bundle Package Install
- V-Key Credential Provider
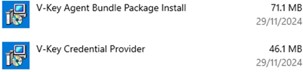
Fig 18: Uninstall Windows Logon
After that check the V-Key Windows Logon option is not shown for login anymore

Fig 19: Windows Logon Uninstalled
Appendix
Directory Configuration
- Login IDM Portal with admin account Navigate to Directories page & select [Create]
Fig 20: Create Directory
Select directory type as [V-Key AD]
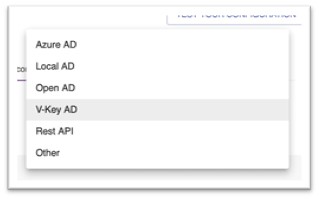
Fig 21: Select Directory
- Select to edit created directory to create users under the directory. You may create users manually or import through a .csv file.
- Input suitable name for directory & Click Save. The Directory will be saved successfully
Select [Add User] for manual entry of users.
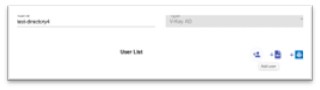
Fig 22: Add Users
- Input all required fields and save User successfully.
- Check the mailbox of created user to make sure that new account receives an email from V-OS Cloud.
At V-Key AD directory page, select to test configuration. Input login credentials of
created account & test.
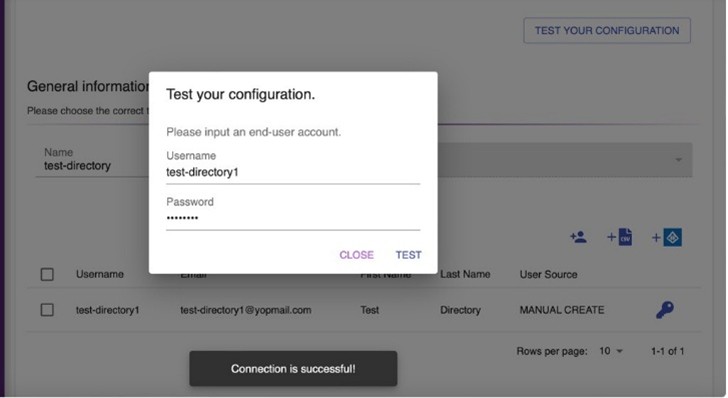
Fig 23: Test Account
- You may also import users from csv file for batch upload. Click Import CSV button. Download ‘Import-Template.csv’ file
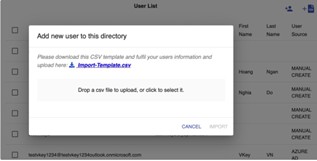
Fig 24: Download CSV Template
Fill the user’s information into the csv file
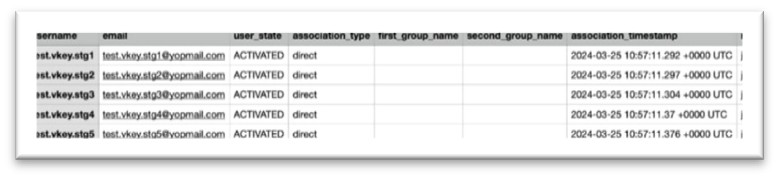
Fig 25: CSV Format
- Upload csv file then import it
- Check the users are imported with user source as [CSV Import]
- You may import batch users using Azure AD. For that you should have Azure AD admin account and required setup for Azure AD
- Click on [Import Azure] button
- Then continue by clicking on the Authorize button.
Submit Azure admin credential to login
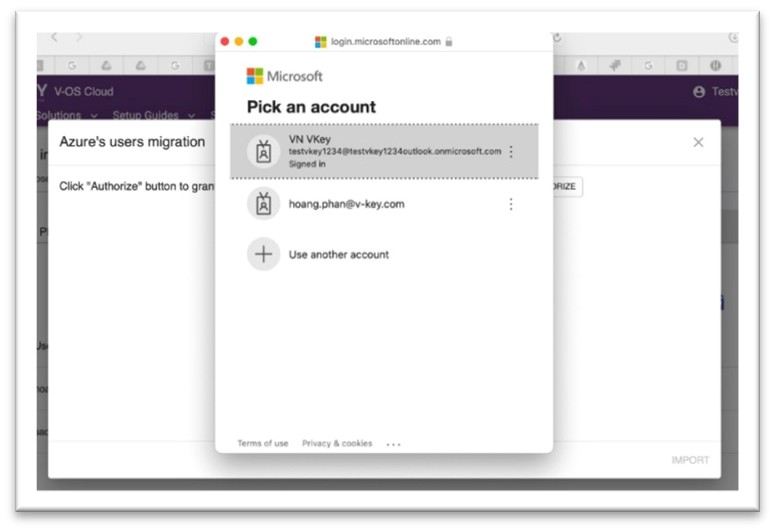
Fig 26: Azure Admin Login
After successful authorization, users are selected to migrate. Select the users then click ‘Import’ button and observe the process complete.
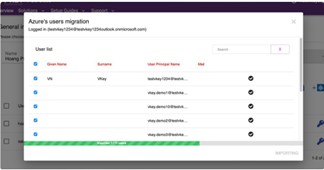
Fig 27: Azure AD Users
- After import, check the imported users with the [User Source] as [Azure AD]
Token Pack Configuration
The token pack is a unique profile used by V-OS Cloud IDM to identify organizations and environments that V-OS Cloud connecting to. It is based on the connectors and services you configured through V-OS Cloud Dashboard.
The token pack is presented in a form of a QR code and keeps information like ID, name, logo, theme, and configuration information that help the V-Key app identifies the organization that the app users belong to while onboarding to V-OS Cloud services. This code is generated from V-OS Cloud Dashboard and sent to app users for service onboarding. This code is necessary for app users to activate accounts. To use the QR code, app users use the V-Key Smart Authenticator (VSA) app (available in app stores) to scan this code to activate his/her account.
To create and configure a token pack, do the following steps:
- Log in to the V-OS Cloud Dashboard with an admin account.
- Click Token Packs on the left sidebar.
- Click the “pencil” icon of the pre-generated token pack from the list.
Fig 28: Token Packs
- Assign a Name to the token pack for easy identification, e.g., Service Token Pack. This can be any name.
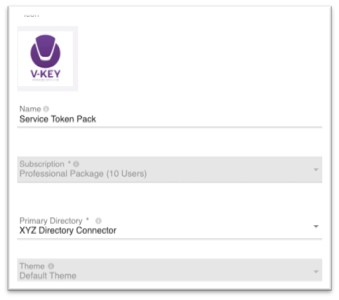
Fig 29: Edit Token Pack – Connector
- Click the icon field and assign an icon to the token pack, if desired.
- Select the Primary Directory and Theme to be assigned to the token pack from the respective dropdown.
Note: The Primary Directory is the directory used for authenticating users of the V-Key app. It can be the same or different directory configured in the service instance. The Theme is the theme that you wish to apply to your V-Key app when this token pack is used. You can configure different themes for different token packs.
- Pick the desired Service that you want to enable in the token pack.
Note: A token pack can contain the services for multiple services. If you are intending to have multiple services under the same token pack, select the service accordingly by toggling the “power plug” icon.
- Click [Save] to create the token pack.
